Developing a Structured Approach to Cybersecurity
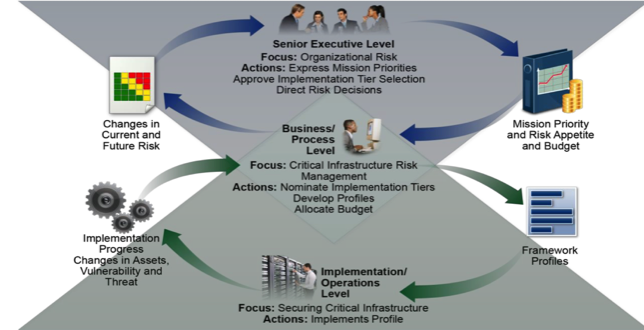
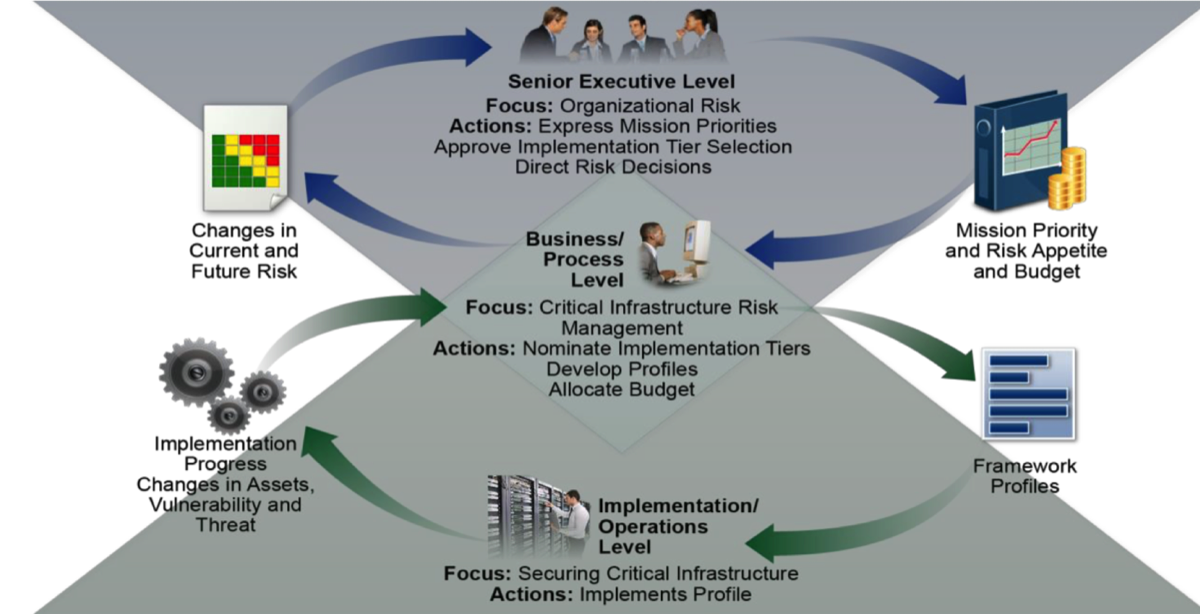
This is the same risk management approach - and used the same set of familiar tools and processes - as is commonly used in most corporations as a part of their standard operating procedures. As a certified Project Management Professional I can attest to the fact that these are the very same procedures and steps take when managing any of my contracts or projects.
Recognizing this link between cybersecurity and risk management is essential when one try's to make heads or tails of the myriad publications (NIST 800-xxx) and guidelines published.
A common failing by many who try to explain Cybersecurity is that it is essentially a Risk Management exercise with some new terminology.
Author

Here's the way to use this handbook as part of a structured approach:
- Determine who your customer is. If it is NOT the Department of Defense you are looking at a much lower set of requirements. Those are the ones listed as the The 15 Essential Requirements of FAR 52.204-21 on the Requirements tab in this section. If your customer IS the Department of Defense or if they are doing a "me too" on the DFARS requirements then you will have a more extensive list of requirements.
- For the FAR only crowd the charts included in the "Requirements" section are keyed to the numbered sections in the Self Assessment Checklist. So start with those 15 requirements and cross reference to the NIST Handbook 162 for the corresponding section(s). For example the FAR Requirement is the table shows 3.1.1 Limit system access to authorized users, processes acting on behalf of authorized users, or devices (including other systems) as the first requirement. If you turn to page 8 in the self assessment checklist you will find a list of questions and answers that will assess your current cybersecurity readiness and provide a roadmap when completed of follow-up actions you'll need to complete.
- Record your responses on the Excel worksheet included in the Downloads page of this website to provide a comprehensive record of your results.
- Transfer the questions or areas where you do NOT meet requirements to list or Excel worksheet. This is both a punch list and the beginning of a Risk Matrix. More about that below.
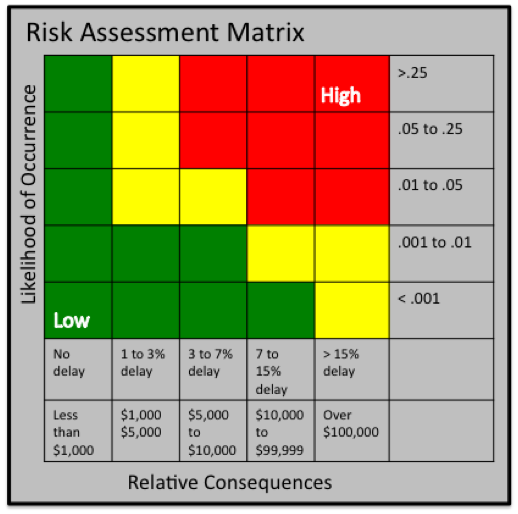
- Is this "risk" a good thing or a bad thing? Does it potentially harm your business or is it an opportunity that could perhaps be exploited?
- What is the likelihood this risk will come to pass? This is a subject measure at this point but you should agree with other members of the team what various ratings like "Very Low". "Low", "High" etc. mean and apply the measurement consistently. Often this is done with a numeric value like 1 … 5
- Now consider what is likely to happen if worst comes to worst. For example if someone gets unauthorized access to your system what damage could they do? Erase files? Divulge sensitive information on the internet. Encrypt your drive and hold its contents for ransom? Again you should evaluate each of the possible risks and assign a value using the same approach as before from 1 …5
- To score the risks you should multiply the number from "likelihood" (#2) by the "outcome" (#3) to get a score between 1 and 25 (5 x 5 =25).
- You can also plot the results on a "Heat Map" to visually display the criticality of each uncompleted item in your checklist.
The above technique is very subjective and can easily be manipulated for evil intent. But if you do an honest assessment you should end up with a rank ordered list of items that need to be addressed such that if you use a "squeaky wheel" approach the highest scores get addressed first and the lesser scored items can take a bit longer.
Understanding the Limits of the Preceding Approach
As stated earlier the subjective approach (called Qualitative Analysis) described above is pretty easy to manipulate and often does not give satisfactory results. This is because we are attempting to use a single value to something that is not easily quantified. Often times the likely outcome can vary across a broad range as shown in the below example. How do you quantify something that could be 600 dollars or ruin your company? It's hard to express that with a single value - although we often try to do so.
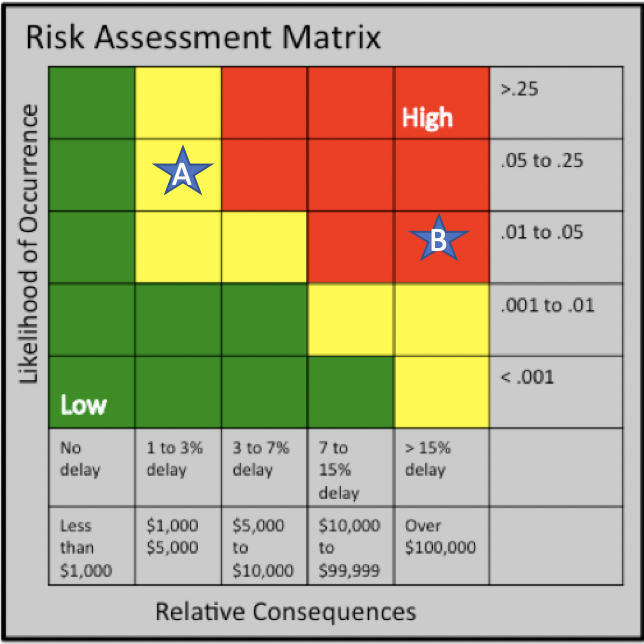
Consider this example
Example A :
Example B :
Which scenario is the higher risk and which would you address first?
Example A :
- Loss of a company laptop or cell phone – 5 to 10% likelihood
- Replacement cost - $600 to $1200
Example B :
- Lost laptop found (or taken) by someone with malicious intent 1-3%
- Hacks into company network and accesses confidential information that is posted to internet - $100,000,000 damage and loss of reputation
Which scenario is the higher risk and which would you address first?
There are advanced techniques (Quantitative Analysis) that can be used to do more in-depth analysis of these factors but for our level of understanding we only need some relatively crude data. The first is ordinal - which risk is most serious from a cost and likelihood point of view.
Step One. Identify and Rank Order the Risks - which we just did.
Step Two. Identify the best (for your business and your circumstances) way to counter that risk. You can use any number of techniques including Avoidance, transference, mitigation, etc. But each possible solution has a cost. So what's the cost of the solution when compared to the risk? If the cost of prevention is more than the cost of the loss …. You get my point.
Step Three. Implement the solution
Step Four . Monitor results and evaluate risks periodically
Step Fife. Adjust your approach to match the changing threat landscape.
Step One. Identify and Rank Order the Risks - which we just did.
Step Two. Identify the best (for your business and your circumstances) way to counter that risk. You can use any number of techniques including Avoidance, transference, mitigation, etc. But each possible solution has a cost. So what's the cost of the solution when compared to the risk? If the cost of prevention is more than the cost of the loss …. You get my point.
Step Three. Implement the solution
Step Four . Monitor results and evaluate risks periodically
Step Fife. Adjust your approach to match the changing threat landscape.
